Incident Overview
Since 6 PM Beijing Time on December 4, 2024, “ghost repositories” have been appearing on GitHub. These repositories contain no code but include deceptive virus files. That same day, they became the fastest-growing repositories on GitHub in terms of stars. Over 180 fake zombie accounts were spreading the virus, waiting for victims to fall into their trap.
A Chinese developer—myself—took notice of all this. After days of probing and searching, I identified the attacker.
Incident Details
Initially, I was developing an open-source program to identify early-stage potential seed projects. Source code: https://github.com/chmod777john/github-hunter
During the search on December 4, I came across a series of unusual repositories.
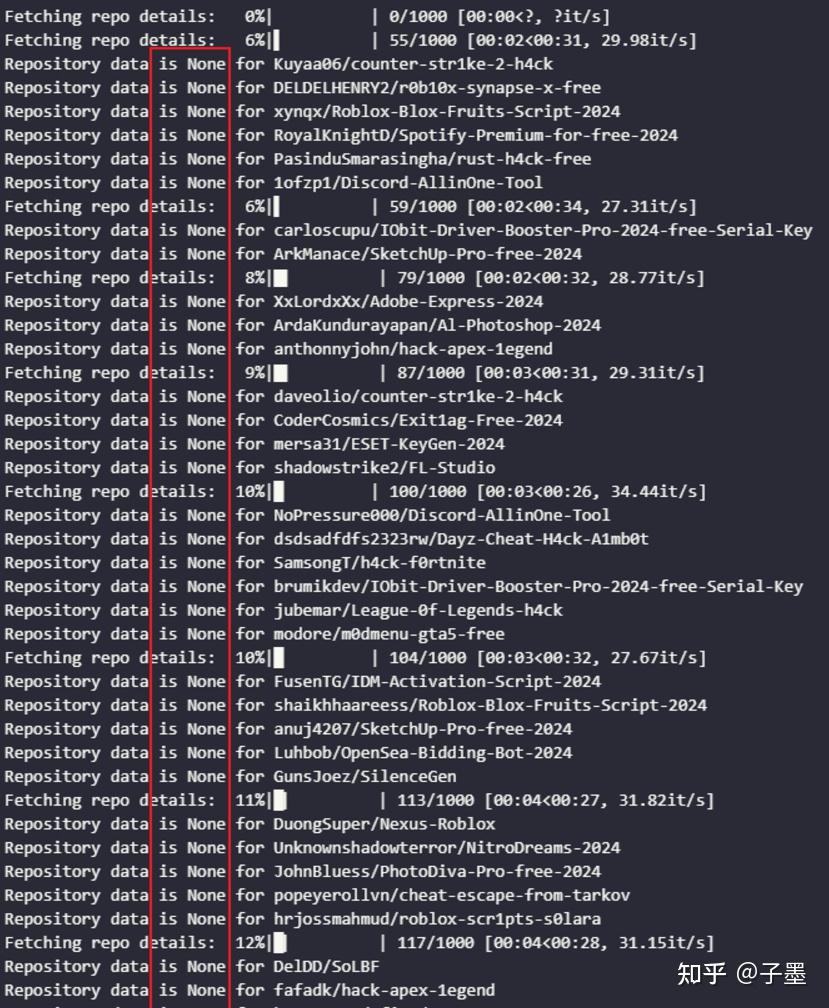
The term is None here refers to repositories with a significant number of star records that were later deleted. Why would such a large number of highly-rated repositories be removed?
Initially, I didn’t pay much attention to it, but a day later, these repositories reappeared.
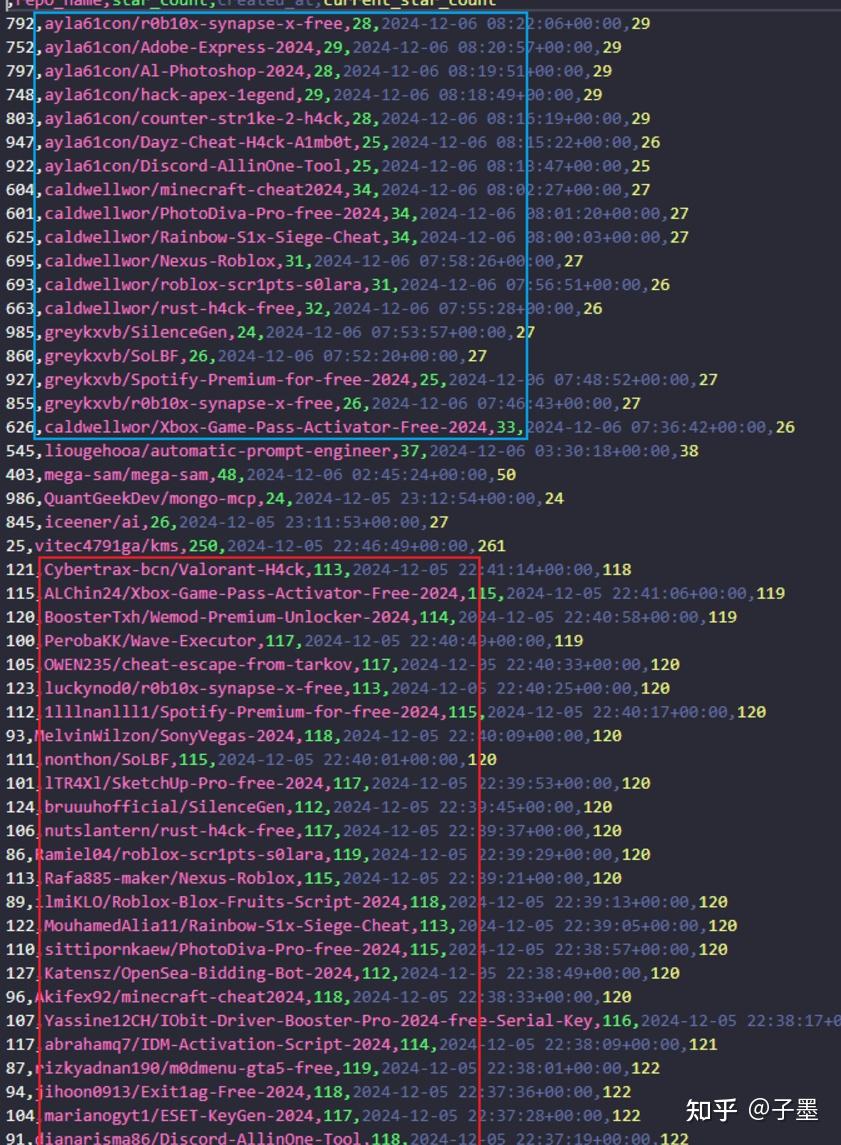
Just like ghosts, they follow a pattern: creating repositories -> gaining high star counts -> deleting repositories -> recreating them.
Evidence
When you take a closer look at these repositories, they all share a similar theme: claiming to be cheats for certain games or cracked versions of software like Photoshop, enticing users to download and run their .exe files.
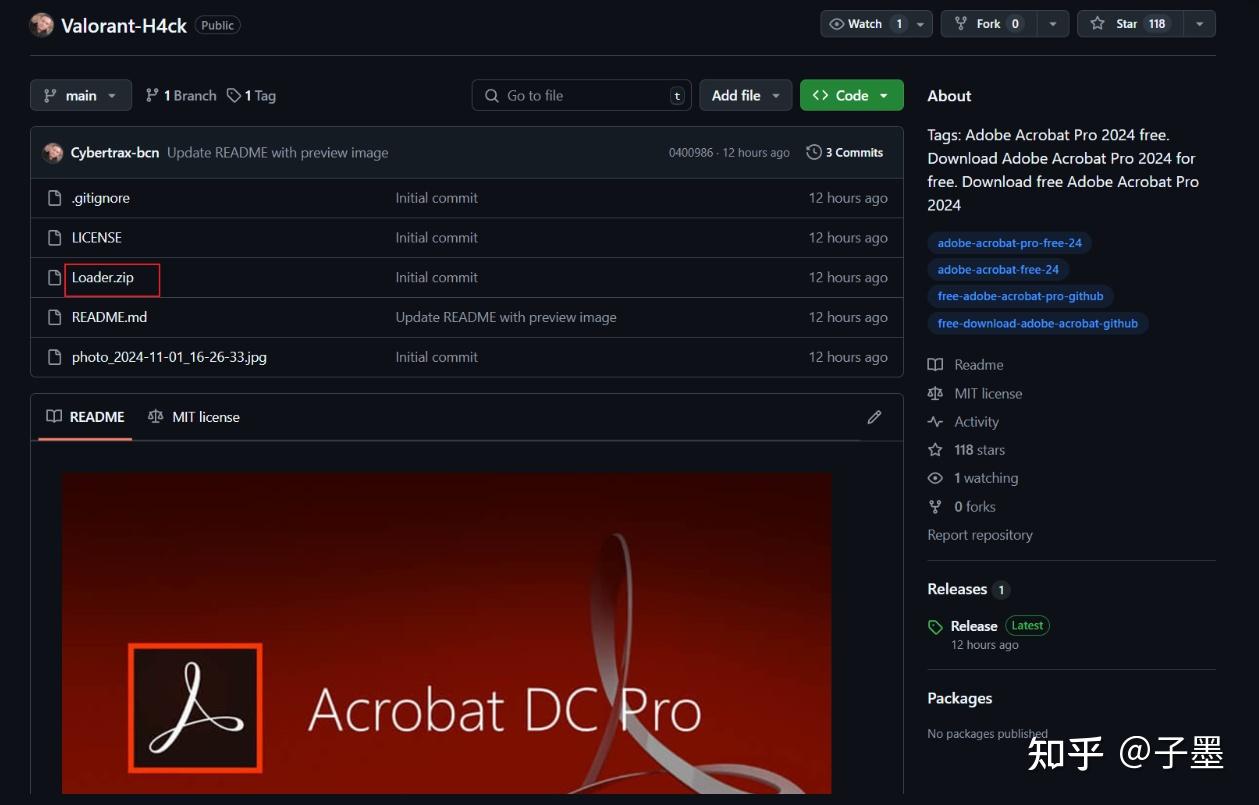
It can be basically confirmed that these are phishing repositories. All these repositories were created around the same time, approximately ten hours ago, and accumulated hundreds of stars in a very short period, suggesting the work of skilled individuals.
Tracking the Culprit
Who are these attackers? I decided to investigate further.
An Attack Spanning Four Years
The first step was to look at who starred these repositories.
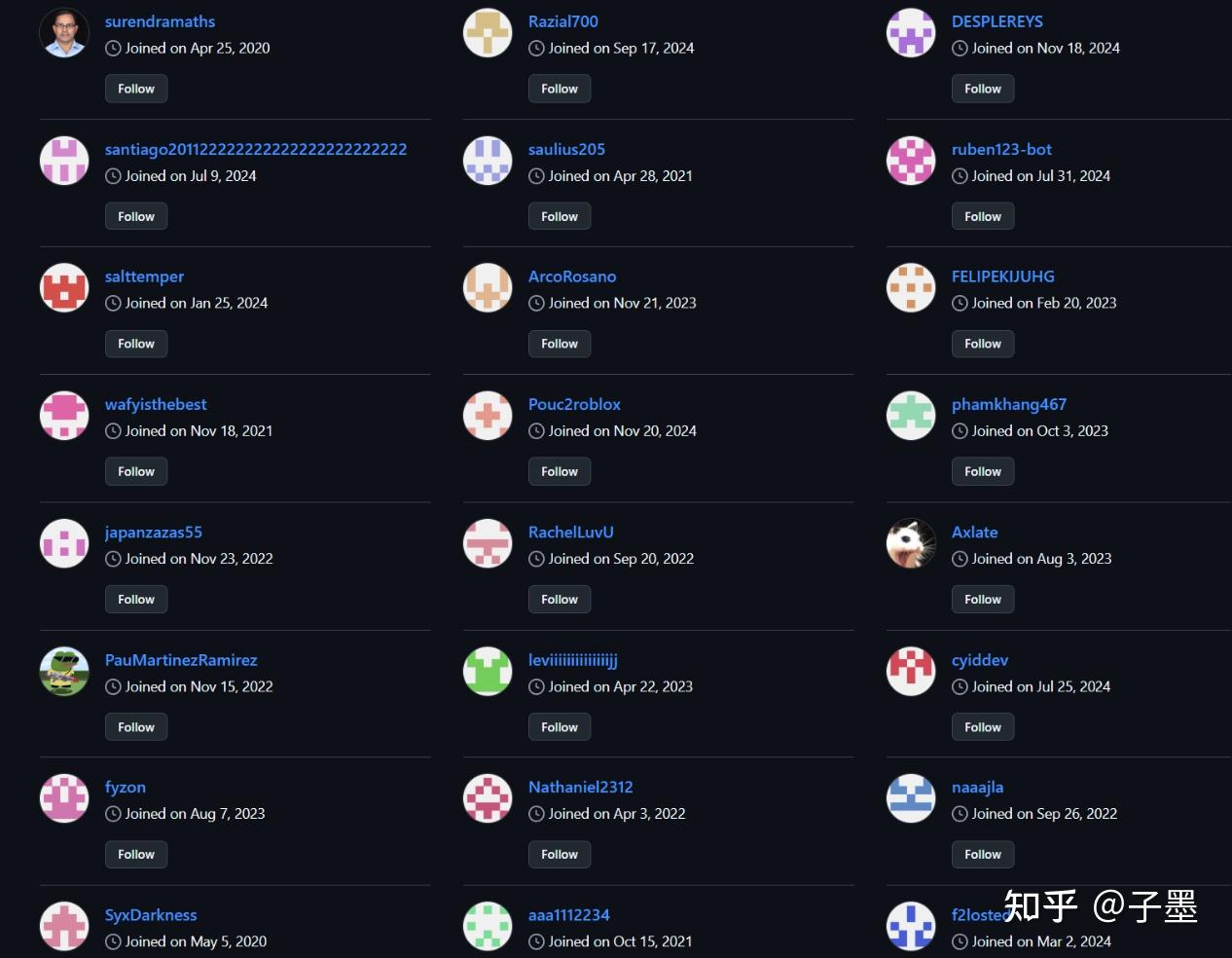
I initially assumed that most of these were newly created bot accounts.
Surprisingly, these accounts were not recently created. Some of them had joined GitHub as far back as 2020.
A four-year-old account isn’t something casually made. If the attacker cultivated these accounts personally, that would represent a significant investment—nurturing an account for four years just for this moment.
If these accounts were purchased from a black market, it would suggest that people began mass-creating accounts for resale at least four years ago, which points to a well-established industry chain (and one with more longevity than many startups).
Regardless of whether the accounts were self-maintained or purchased, the costs involved are substantial.
A Blank Slate
I started opening these accounts one by one and confirmed one thing: all these repositories were part of the same group!
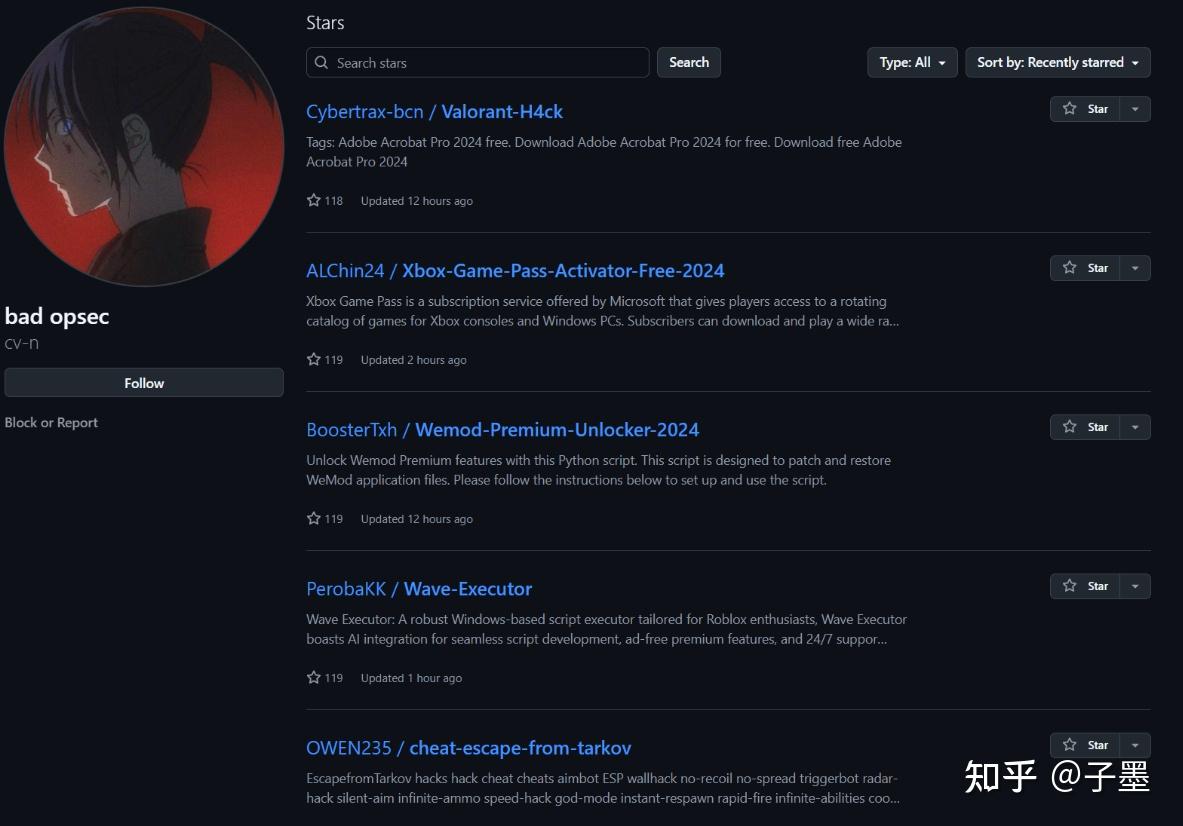
All the repositories that this person liked turned out to be the aforementioned “ghost repositories”!
However, their personal profile was entirely blank. No followers, no following—leaving no leads to trace. It was a complete void.
A Long Road Ahead
I opened all 180+ accounts one by one. Most were purely blank accounts used solely for liking repositories. Still, a few of them had personal profiles.
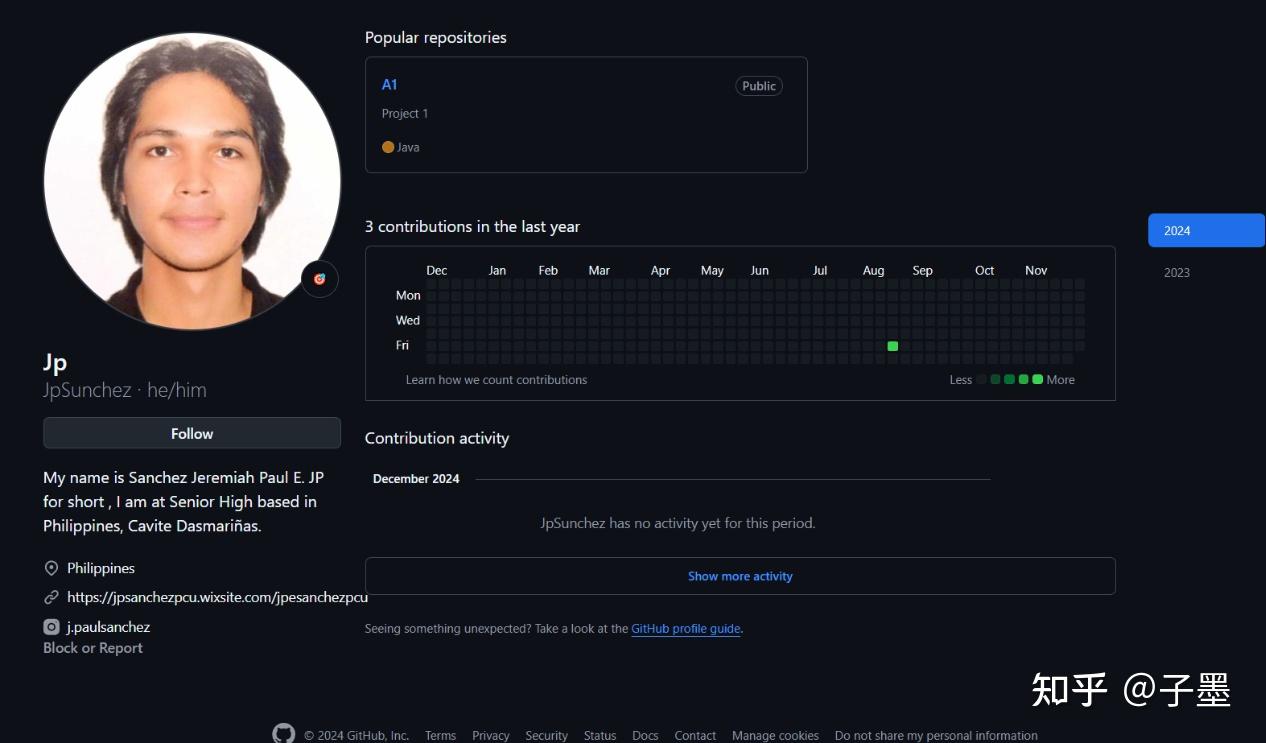
This account even included a personal website and an Instagram profile.
However, everything requires mutual confirmation. What if this account was simply impersonating someone else? For now, it can only be classified as a suspect.
A Turning Point
Who the attacker’s account follows doesn’t matter much, as they could easily fake this information. The truly useful clue is to see who follows the attacker.
After painstaking searching, I finally found a real, active account!
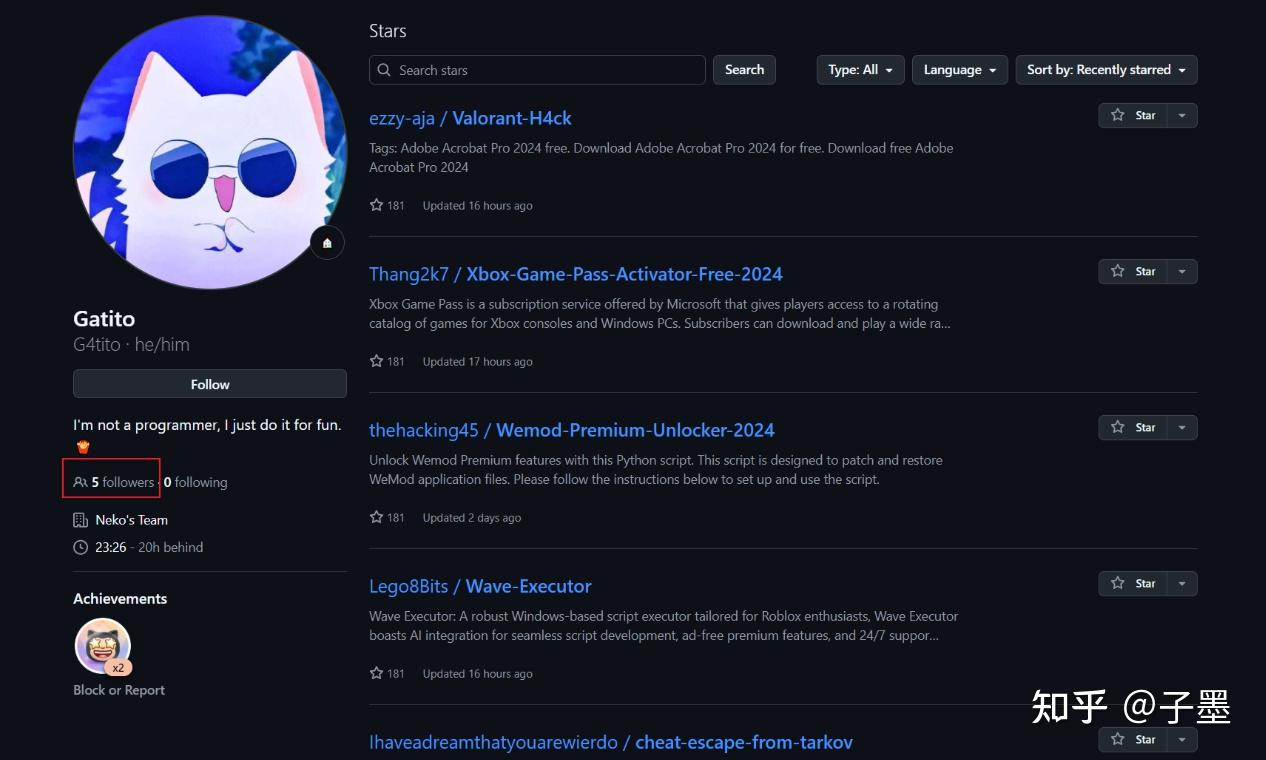
Five individuals followed this account! By examining its star history, it became evident that this user was one of the attackers.
Moreover, the account had genuine GitHub commit records. Remember this specific repository: Simple-WaBot.
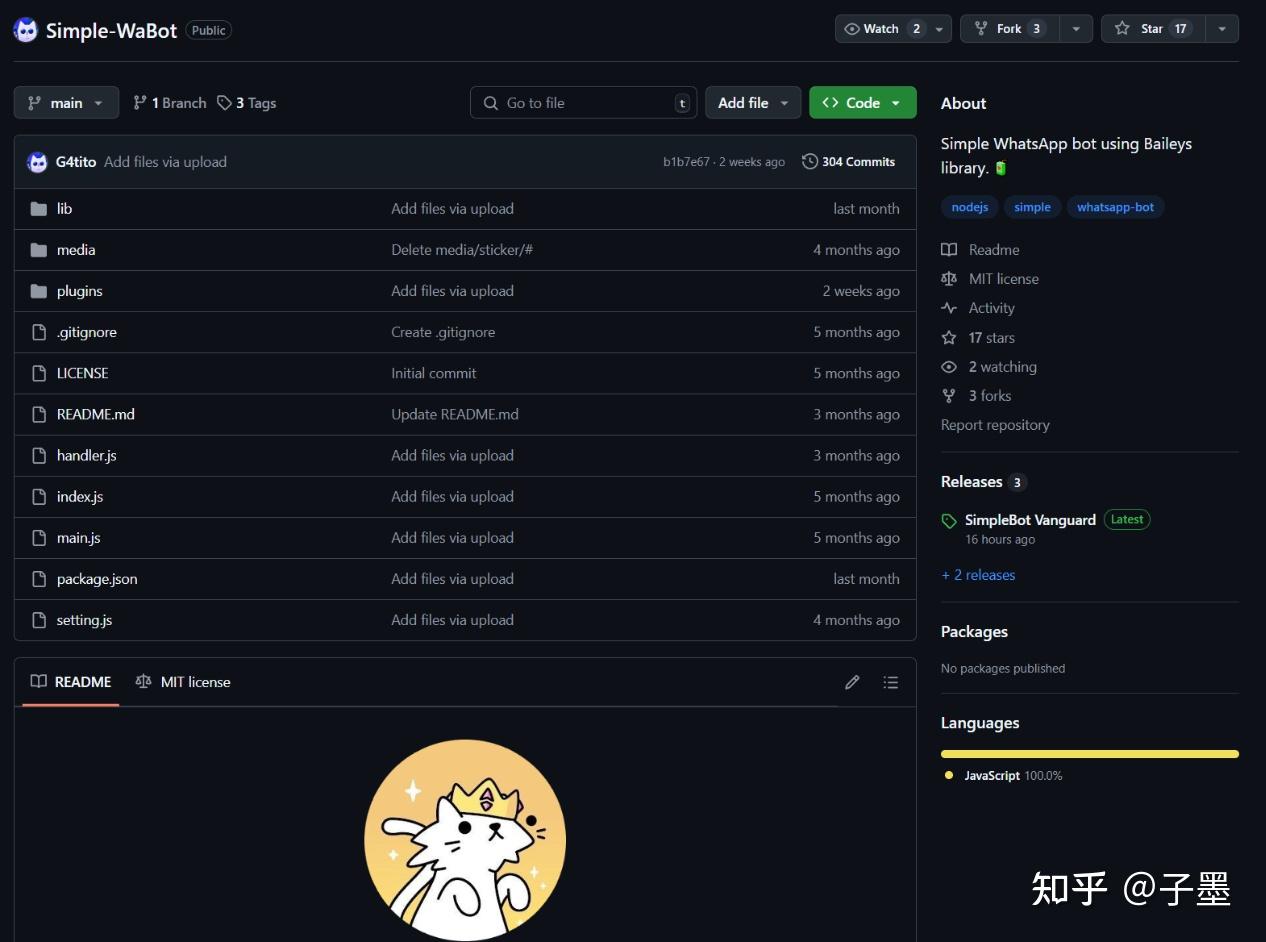
Let’s take a look at who has followed G4tito. This could potentially unveil further connections, leading us closer to uncovering the network or individuals involved in this suspicious activity.
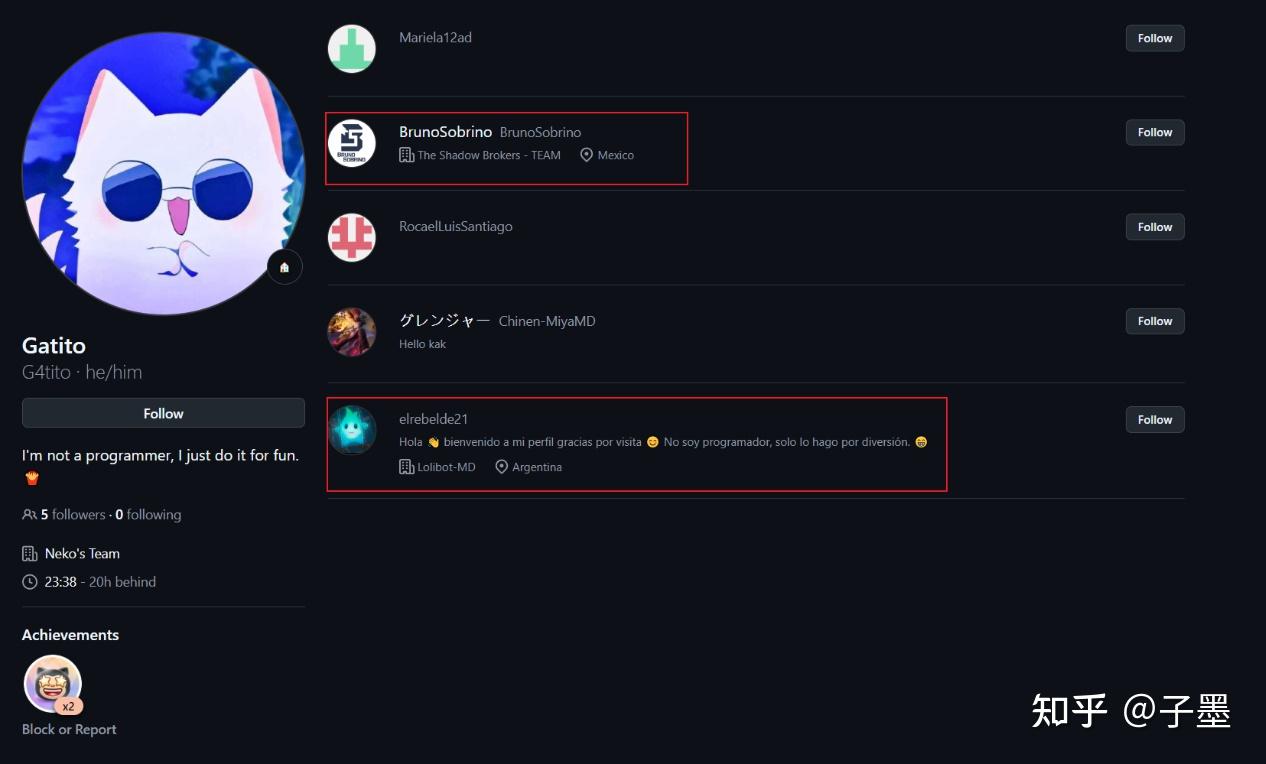
These two individuals are key figures. Let’s examine their GitHub profiles to gain further insights into their activity and potential involvement.
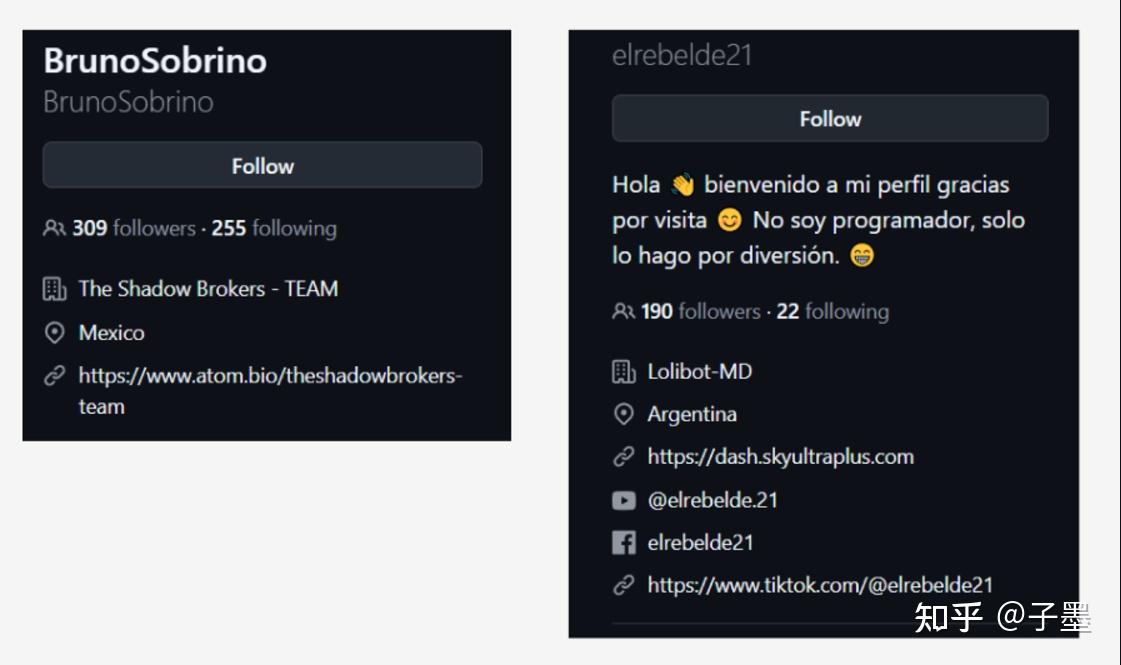
BrunoSobrino and elrebelde21, two prominent figures, once collaborated on an open-source project together.
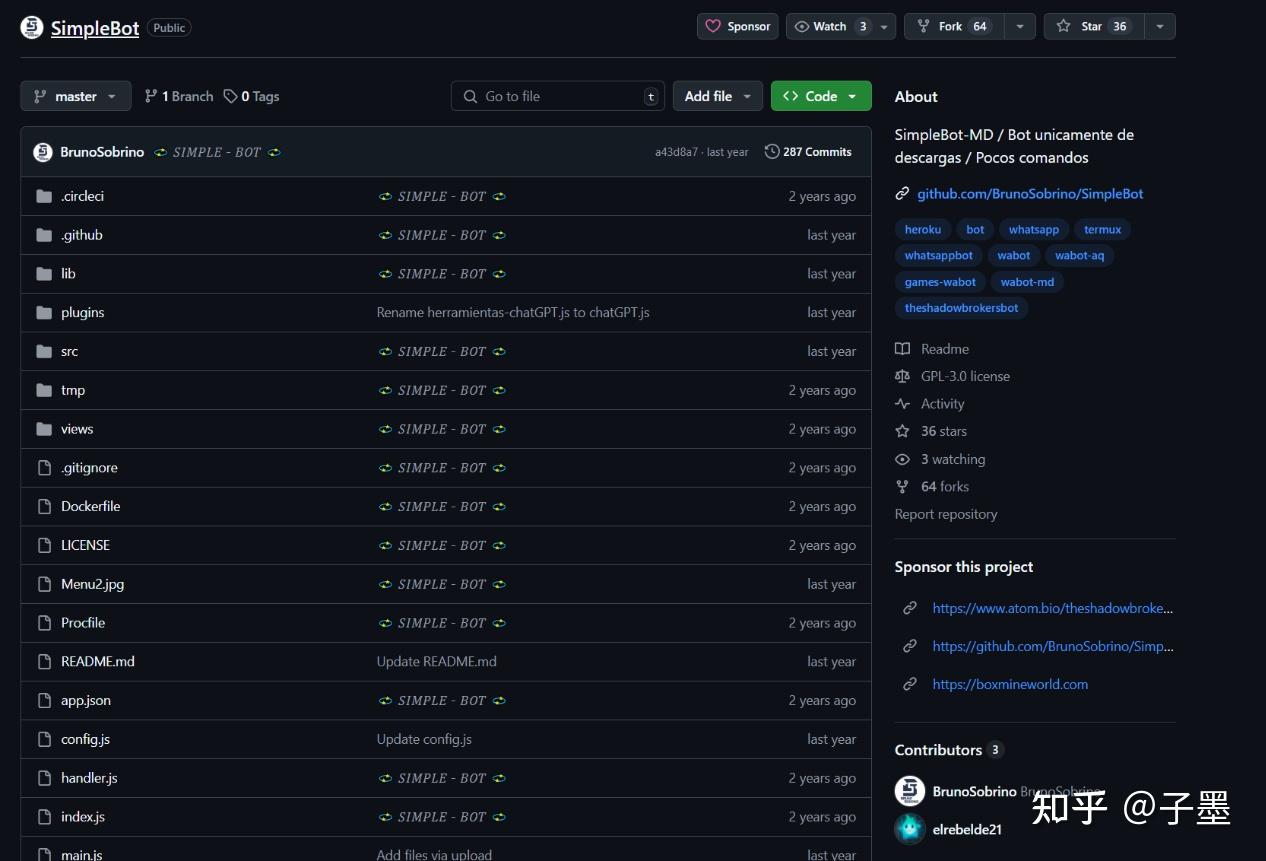
And the project is named identically to the one explicitly linked to the attacker.
At this point, the logical chain is as follows:
It appears that BrunoSobrino and elrebelde21, these two prominent figures, may have connections to the attacker G4tito.
At this point, the case is essentially solved. Manipulating over 180 accounts to like repositories and create them in a short timeframe—along with generating bulk content—is unlikely to have been done manually. Instead, it likely involved automation using the GitHub API. Additionally, the projects these two prominent figures and the identified attacker are engaged in revolve around WhatsApp bots, and their technical stacks align closely.
Update at 6:11 AM on December 7, 2024
After insights from the comments section, a potential lead has been discovered.

Address
https://github.com/BrunoSobrino/ShadowBotV3
GhostArchive Backup Address
https://ghostarchive.org/archive/1EZ9e
Given that they are likely to delete their repositories after exposure, I have proactively backed up all relevant pages to GhostArchive.
Additionally, the malicious repository list I uncovered has been stored on the blockchain as undeniable evidence.
You don’t have to take my word for it—directly verify the information via the blockchain. All records can be viewed here: https://viewblock.io/arweave/tx/Cppr-Bus0TxC6_zqD-sJitVz4Ne3sR0noJknsuyhZ4Q
Note: This post is authorized by original author 子墨 to translate and republish. Original post is at 危机13小时:追踪一场 GitHub 投毒事件
